Trigger warning: The follow post contains disturbing descriptions of scenarios involving child exploitation.
“It’s more than just images. When I’m in public… it’s something like, ‘Have they seen a picture of you when you were a kid?’… It just sucks that it’s still going on, because the pictures are still circulating. It’s like another form of abuse… If those were pictures of you, you would understand.” -Survivor whose childhood sexual abuse was documented and distributedKeller, M. H., & Dance, G. J. X. (2019). ‘If those were pictures of you, you would understand’. The New York Times Retrieved from https://www.nytimes.com/2019/11/09/us/online-child-abuse.htmlCopy
Every nine minutes in the U.S., child protective services substantiates a claim that a child has been sexually abused.United States Department of Health and Human Services, Administration for Children and Families, Administration on Children, Youth and Families, Children’s Bureau. (2018). Child maltreatment survey. Retrieved from https://www.rainn.org/statistics/children-and-teensCopy Considering how many cases are never brought forward, child sexual abuse is a pervasive issue that grows in the shadows.
The survivors often grapple with the effects of abuse for the rest of their lives long after it has ended. Unfortunately, an increasing number of survivors find that even if they’re physically safe, the abuse still continues in the form of child sexual exploitation material (CSEM)—often referred to as “child pornography”—that captured their abuse and mistreatment.
What is “child sexual exploitation material”?
According to ECPAT and INTERPOL, “‘Child sexual abuse material’ (CSAM) refers to material depicting acts of sexual abuse and/or focusing on the genitalia of the child,’ while ‘child sexual exploitation material’ (CSEM) encompasses all sexualized material depicting children, including ‘child sexual abuse material.'”ECPAT & INTERPOL. (2018). Towards a global indicator on unidentified victims in child sexual exploitation material: Summary report. INTERPOL. Retrieved from INTERPOL International Child Sexual Exploitation Database Retrieved from https://ecpat.org/wp-content/uploads/2021/05/TOWARDS-A-GLOBAL-INDICATOR-ON-UNIDENTIFIED-VICTIMS-IN-CHILD-SEXUAL-EXPLOITATION-MATERIAL-Summary-Report.pdfCopy
While “child pornography” remains the legal term for sexually explicit content depicting minors, it refers to a form of child exploitation that often shows violent, degrading, and horrific forms of child abuse. For this reason, survivors and advocates usually use the above terms, CSAM and CSEM, which more accurately convey the seriousness of the content. Plus, using the phrase “child pornography” can make it sound like the child participated willingly, while “CSEM” makes it clear that the child is not the source of the problem.
According to a 2018 study of CSAM survivors, many reported that the images of their abuse caused different distress than the sexual abuse itself.Gewirtz-Meydan, A., Walsh, W., Wolak, J., & Finkelhor, D. (2018). The complex experience of child pornography survivors. Child abuse & neglect, 80, 238–248. https://doi.org/10.1016/j.chiabu.2018.03.031Copy They frequently experienced difficulties, worrying that they would be recognized from the images, or that someone would think they willingly participated in the abuse.Gewirtz-Meydan, A., Walsh, W., Wolak, J., & Finkelhor, D. (2018). The complex experience of child pornography survivors. Child abuse & neglect, 80, 238–248. https://doi.org/10.1016/j.chiabu.2018.03.031Copy
For survivors whose sexual abuse has been filmed and distributed, their abuse is perpetuated again and again and again. What happened to them is not something that remains buried in the past, it’s an ongoing form of distress to know that the worst moments of their lives are still being shared for others’ entertainment and pleasure.
How common is CSEM?
In 2018, tech companies reported more than 45 million images of child sexual exploitation—more than double the number of images found during the previous year.Keller, M. H., & Dance, G. J. X. (2019). The internet is overrun with images of child sexual abuse. What went wrong?. New York Times Retrieved from https://www.nytimes.com/interactive/2019/09/28/us/child-sex-abuse.htmlCopy In 2020, the number of files reported jumped to 65.4 million.National Center for Missing and Exploited Children. (2021). Reduce child sexual exploitation. Retrieved from https://www.missingkids.org/content/ncmec/en/ourwork/impact.html#reduceexploitationCopy The issue of CSEM is not a small problem, it’s a problem of epidemic proportions that grows exponentially every year.
Many reports of CSEM come from tech companies like Facebook and Microsoft who use hashing technology to scan for known images of child sexual exploitation uploaded by users to their servers. In other words, known CSEM images can be fed into a “hashing function,” which creates a unique digital fingerprint—or “hash”—that looks like a jumble of letters and numbers. Then by scanning for that specific fingerprint, tech companies can use AI to find, remove, and report any instances of CSEM that happen on their platform.
However, with increasing concerns about privacy from users, many companies are moving toward end-to-end encryption. While this system would protect users, it would halt millions of CSEM reports, potentially leaving countless survivors at risk.
In response to these proposed changes, the National Center for Missing and Exploited Children (NCMEC)—which runs the United States’ centralized system for reporting and removing CSEM—estimates that more than half of the reports it processes will disappear entirely with end-to-end encryption.National Center for Missing and Exploited Children. (2021). End-to-end encryption: By the numbers. Retrieved from https://www.missingkids.org/theissues/end-to-end-encryption#bythenumbersCopy Experts estimate that victims may have less of a chance of being identified and protected if tech companies comply with calls for encryption.
How does CSEM happen?
According to research and the experiences of survivors, producers of CSEM can be anyone—a friend, family member, or even the child themselves.
When imagining perpetrators of child sexual abuse, some may automatically conjure stereotypical images of a creepy guy in a white van who offers kids candy on their way home from school. But the unfortunate fact is that most victims of child sexual abuse are abused by a trusted adult.Lanning, K. V. (2010). Child molesters: A behavioral analysis for professionals investigating the sexual exploitation of children. (No. 5). National Center for Missing & Exploited Children. Retrieved from https://www.missingkids.org/content/dam/missingkids/pdfs/publications/nc70.pdfCopy
In fact, research reveals that victims of CSEM are commonly abused by their own parents or parental figures.Salter M et al. (2021). Production and distribution of child sexual abuse material by parental figures. Trends & issues in crime and criminal justice no. 616. Canberra: Australian Institute of Criminology. https://www.aic.gov.au/publications/tandi/tandi616Copy
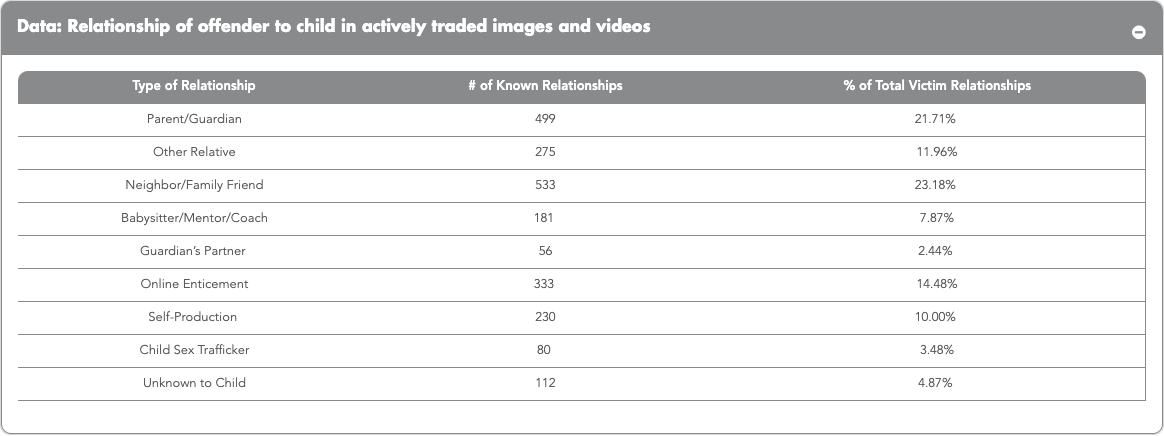
According to data from the National Center for Missing and Exploited Children (NCMEC), more than 1 in 5 identified victims in actively traded CSEM were abused by a parent or guardian, nearly 1 in 4 were abused by a family friend or neighbor, and approximately 1 in 7 were exploited through online enticement. Only 4.87% were abused by a stranger.National Center for Missing and Exploited Children. (2021). Reduce child sexual exploitation. Retrieved from https://www.missingkids.org/content/ncmec/en/ourwork/impact.html#reduceexploitationCopy
When abuse by a stranger does happen, online enticement is an increasingly common way that predators exploit children, with reports showing that the grooming and luring of children is increasingly happening online.International Centre for Missing and Exploited Children. (2017). Online grooming of children for sexual purposes: Model legislation & global review. ( No. 1). Retrieved from https://www.icmec.org/wp-content/uploads/2017/09/Online-Grooming-of-Children_FINAL_9-18-17.pdfCopy
So while images of strangers in vans may still linger in the public’s mind, those scenarios are rare in comparison to the number of predators who have moved online. Using social media or other communication apps, predators can groom children from afar. Some even pose as a peer of the child, become their “friend,” and eventually ask for sexual images.
For example, after encountering a devastating case of an online predator grooming and abusing a 12-year-old girl online, Bark Technologies put together a special projects team. Their team created fake accounts posing as young girls to illustrate to parents, guardians, and schools the severity of the problem.
Less than a minute after launching an Instagram account for a fictional 11-year-old girl named Bailey, Bailey’s photo had been liked by an account whose profile picture was a penis. In under two minutes, Bailey had received three message requests. Within five minutes, an adult man was video-calling her. And in two hours, she’d received 15 messages from adult men—half of whom could be charged with transferring obscene material to a minor.Bark (2020). Social Media Dangers Exposed by Mom Posing as 11-Year-Old. YouTube, YouTube, 20 Feb. 2020, https://www.youtube.com/watch?v=dbg4hNHsc_8Copy Ryan, S. (2019). I’m a 37-year-old mom & I spent seven days online as an 11-year-old girl. Here’s what I learned. . Medium Retrieved from https://medium.com/@sloane_ryan/im-a-37-year-old-mom-i-spent-seven-days-online-as-an-11-year-old-girl-here-s-what-i-learned-9825e81c8e7dCopy
The term “CSEM” also includes self-generated material, or sexual content that the child created of themselves. This is a growing trend in the world of CSEM, given the prevalence of sexting and sending nudes.Thorn. (2020). Thorn research: Understanding sexually explicit images, self-produced by children. Retrieved from https://www.thorn.org/blog/thorn-research-understanding-sexually-explicit-images-self-produced-by-children/Copy Most minors who send nudes are unaware of the potential risks, or the fact that sending sexual images of themselves counts as the distribution of CSEM.
According to one report, approximately 1 in 5 girls and 1 in 10 boys aged 13-17 report sharing their own nudes.Thorn. (2020). Thorn research: Understanding sexually explicit images, self-produced by children. Retrieved from https://www.thorn.org/blog/thorn-research-understanding-sexually-explicit-images-self-produced-by-children/Copy That’s especially concerning considering that 1 in 3 underage teens report having seen nonconsensually shared nudes of other minors—all of which qualifies as CSEM.Thorn. (2020). Thorn research: Understanding sexually explicit images, self-produced by children. Retrieved from https://www.thorn.org/blog/thorn-research-understanding-sexually-explicit-images-self-produced-by-children/Copy
That shows that even when minors are sending their images to someone they know and trust, it’s not uncommon for those images to end up in the wrong hands. In fact, over 90% of police officers report that self-generated images are common in their investigations of CSEM.NetClean. (2018). NetClean report 2018: A report about child sexual abuse crime. Retrieved from https://www.netclean.com/wp-content/uploads/sites/2/2018/12/The-NetClean-Report-2018_Web.pdfCopy
So between online predators grooming kids to send CSEM and the normalization of sexting between minors, kids are at greater risk for CSEM victimization than ever.
How are mainstream porn and CSEM connected?
The unfortunate fact is that even the mainstream porn industry has a history of profiting from CSEM, sometimes even ignoring victims’ pleas to remove abusive content.Kristof, N. (2020). The children of Pornhub. New York Times. Retrieved from https://www.nytimes.com/2020/12/04/opinion/sunday/pornhub-rape-trafficking.htmlCopy Kristof, N. (2021). Why do we let corporations profit from rape videos? New York Times. Retrieved from https://www.nytimes.com/2021/04/16/opinion/sunday/companies-online-rape-videos.htmlCopy
One survey of domestic minor trafficking victims found that of those who had been forced into porn, the average age they began being filmed was 12.8 years old.Bouché, V. (2018). Survivor insights: The role of technology in domestic minor sex trafficking. Thorn. Retrieved from https://www.thorn.org/wp-content/uploads/2019/12/Thorn_Survivor_Insights_090519.pdfCopy One 15-year-old victim, for example, had been missing for a year before she was spotted in a number of videos on a popular porn site—and yes, the account that posted the videos had been “verified.”McDonald, S. (2019). Florida man arrested after 58 porn videos, photos link him to missing underage teen girl. Newsweek. Retrieved from https://www.newsweek.com/florida-man-arrested-after-58-porn-videos-photos-link-him-missing-underage-teen-girl-1467413Copy Cheong, I. M. (2020). Pornhub verified child sex trafficking. Human Events. Retrieved from https://humanevents.com/2020/03/01/pornhub-verified-child-sex-trafficking/Copy
In another incident, a young woman had to contact the police in order to get videos of her as a 16-year-old removed from a verified account on a popular porn site.Gallien, S. (2020). Tuscaloosa man charged for producing porn with a minor, uploading it to PornHub. ABC News. Retrieved from https://abc3340.com/news/local/pornhub-account-tied-to-tuscaloosa-mans-arrest-for-producing-porn-with-a-minorCopy And there have even been reports of child sexual abuse involving small children—in some cases, toddlers still wearing diapers—being uploaded to porn sites and monetized with ads.Gorman, G. (2020). Child abuse victim says porn website Pornhub profited from her child rape. News.Com.Au. Retrieved from https://www.news.com.au/lifestyle/real-life/news-life/child-abuse-victim-says-porn-website-pornhub-profited-from-her-child-rape/news-story/7e3880aa4a94504acea7675bb8112cffCopy
Considering porn’s ability to normalize toxic sexual narratives, it’s especially concerning to note that one of the most consistently popular porn themes is “teen.” One study even found that “teen” is the most common word used in porn titles.Vera-Gray, F., McGlynn, C., Kureshi, I., & Butterby, K. (2021). Sexual violence as a sexual script in mainstream online pornography. The British Journal of Criminology, doi:10.1093/bjc/azab035Copy Research also indicates that teen-themed porn often includes the portrayal of underage individuals, and that this theme is becoming increasingly popular.Walker, A., Makin, D. A., & Morczek, A. L. (2016). Finding Lolita: A comparative analysis of interest in youth-oriented pornography. Sexuality & Culture, 20(3), 657-683. doi:10.1007/s12119-016-9355-0Copy
Plus, it’s worth noting that porn can be so effective at normalizing sexual violence that many sexual predators use porn to groom their victims and desensitize them to sexual advances.International Centre for Missing and Exploited Children. (2017). Online grooming of children for sexual purposes: Model legislation & global review. ( No. 1). Retrieved from https://www.icmec.org/wp-content/uploads/2017/09/Online-Grooming-of-Children_FINAL_9-18-17.pdfCopy Lanning, K. V. (2010). Child molesters: A behavioral analysis for professionals investigating the sexual exploitation of children. (No. 5). National Center for Missing & Exploited Children. Retrieved from https://www.missingkids.org/content/dam/missingkids/pdfs/publications/nc70.pdfCopy
For over 33 years, child abuse expert Michael Sheath has been counseling men who abuse children. He describes a dramatic shift to treating more and more online groomers and downloaders of child abuse images in the last couple of decades. He explains that many of the men he works with don’t seem to be born pedophiles, rather, they’ve gone down an “escalating pathway.”
He continues, “Mainstream pornography sites are changing the thresholds of what is normal and I think it’s dangerous. Of course, most people can watch extreme porn and walk away, but I don’t see those people. What we are seeing on a daily basis is the conflation of easy access to hardcore and [extreme] pornography and an interest in child molestation. The link is unambiguous.”Grant, H. (2020). How extreme porn has become a gateway drug into child abuse. The Guardian Retrieved from https://www.theguardian.com/global-development/2020/dec/15/how-extreme-porn-has-become-a-gateway-drug-into-child-abuseCopy
We want to be very clear that we are not saying that consuming porn will turn people into pedophiles or child abusers. Even so, it is time that we start being more critical of the toxic narratives that mainstream porn is normalizing and recognize the harm it perpetuates in many peoples’ lives. Research is clear that pornography consumption can become an escalating behavior and that it can promote sexual violence.
How you can help
- Educate yourself.
When it comes to issues surrounding child sexual abuse, there’s unfortunately a lot of misinformation. By listening to the experiences of survivors and informing yourself on how these issues play out, you can help stop the spread of misinformation and empower yourself and others with the knowledge needed to advocate in meaningful ways.
If you’re a parent, guardian, mentor, or educator, teach young people how to use social media responsibly to avoid online grooming, and make sure they understand the risks of sending nudes. - Consider before consuming.
It might be time to reconsider how a porn habit may be contributing to the normalization of sexualizing minors. As described above, mainstream porn thrives on the glorification of toxic sexual scripts, but no child’s abuse should be sold as sexual fantasy. There’s virtually no way to guarantee that any porn is truly ethical, let alone legal. We encourage our society to consider how porn objectifies teens and sexualizes abuse, and to focus more on humanizing the young people around them. - Report CSEM if you see it.
To report CSEM, to get help, or to learn more about combating child sexual exploitation, visit the National Center for Missing and Exploited Children’s website at missingkids.org - Have you sent nudes while you were under 18?
As you can see from the surveys above, teens are sending and receiving nudes now more than ever. If you have nudes online from when you were under 18, you’re not alone—there is help to get them removed. Take It Down is a free resource created by the National Center on Missing and Exploited Children (NCMEC) created to help you remove online nude, partially nude, or sexually explicit photos and videos taken before you were 18. You can learn how to use Take It Down, a free, anonymous resource, here. For more victim resources, click here.
Get involved
This is a huge problem in our society and we can’t let it slip into the background. To report an incident involving the possession, distribution, receipt, or production of child pornography, file a report on the National Center for Missing & Exploited Children (NCMEC)’s website at www.cybertipline.com, or call 1-800-843-5678.
To learn how sex trafficking and pornography are connected, click here.
Support this resource
Thanks for taking the time to read through this article! As a 501(c)(3) nonprofit, we're able to create resources like this through the support of people like you. Will you help to keep our educational resources free as we produce resources that raise awareness on the harms of porn and sexual exploitation?
DONATE